The Man In The Disk
If you’ve ever taken an introductory class on cyber security (or if you’ve explored the topic on your own), then you’re likely familiar with the term MITM. Man-In-The-Middle attacks are security breaches where a 3rd party butts their way in-between two parties attempting to communicate. Obviously, this is not an ideal situation for either party, and a new variation of MITM is taking Android users by storm.
MITD
Man-In-The-Disk (MITD) is the name that’s been flying around the past few days. But before we get into its details, let’s discuss a little more of what MITM attacks entail. A MITM attack is when an unknown party inserts itself between the two trying to communicate. When this is done that malicious party is able to spy on the conversation happening. Even worse they might altar what is being sent.
As an example let’s picture an everyday conversation between two friends. Person 1 and 2 are talking to one another about their plans for tonight. And let’s say person 3 is bitter they didn’t get invited. Person 1 might send 2 a message online asking “Want to meet up at 8?”, but 3 intercepts it, changes it, and then forwards the newly modified message to 2. Now when 2 opens the message it instead says “On second thought there are cooler people I’d rather spend my time with”. (A riveting example, right?)
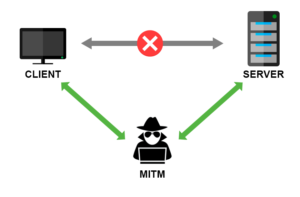 The idea is simply that a 3rd party can both invade and modify conversations between clients and servers. And a lot of the time the invasion can be a lot more critical than hurt feelings. MITM attacks can be avoided by taking proper precautions and such as certificate pinning. But that deserves a whole post of its own.
The idea is simply that a 3rd party can both invade and modify conversations between clients and servers. And a lot of the time the invasion can be a lot more critical than hurt feelings. MITM attacks can be avoided by taking proper precautions and such as certificate pinning. But that deserves a whole post of its own.
So How Does It Happen?
MITD attacks are a specific type of MITM that takes advantage of careless storage on users phones. MITD attacks can allow 3rd party users to access information that is stored on an android device’s external storage. This is something that many apps don’t use, but researchers at Check Point recently found that many app developers (including Google itself) are not following the recommended security precautions for avoiding this vulnerability.
There are a couple different methods for storing information in Android apps. Android’s developer website has a good page laying out the differences between them. If you want to go deeper into when using each is appropriate PhonLab covers this in its Android Development Course. For the most part Android security is very sound due to sandboxing. This is the idea that each app silo’s its information and only makes it available to others if either the user allows it or if both apps are on board for sharing.
External Storage
External storage is essentially a part of the device’s storage card that is shared by all applications. Google suggests that developers should add extra validation if apps utilize this storage functionality. And unfortunately it seems that a lot of apps currently aren’t doing this. Due to prioritization of external storage, data coming in to the phone may be subject to MITM attacks before it even reaches the app meant to use it.
Ironically Google was not following this advice either. Since the report came out they’ve addressed the places where they were falling short, but it seems many other apps have made the same mistake and will be named after they correct their issues.
In conclusion, there is a security scare going around for android apps, but don’t overhype it. If developers take the proper precautions to prevent MITM attacks (something Google explains easily how to do on their site) then this danger fades away. Security is an ever-changing field, but this breach is one that can be easily avoided if developers do their due diligence.


Super Fans always leave a comment :-)